Opportunities for Undergraduate Research in Computer Science
|

|
|
PostersStudents attending HelloResearch have the opportunity to present research they have completed as undergraduate students. Below are the students presenting their research at our Poster Session, along with their research posters. Click on each poster to learn more! |
Indiana University Bloomington
|
Carla Cobb
Computer Science
DePauw University
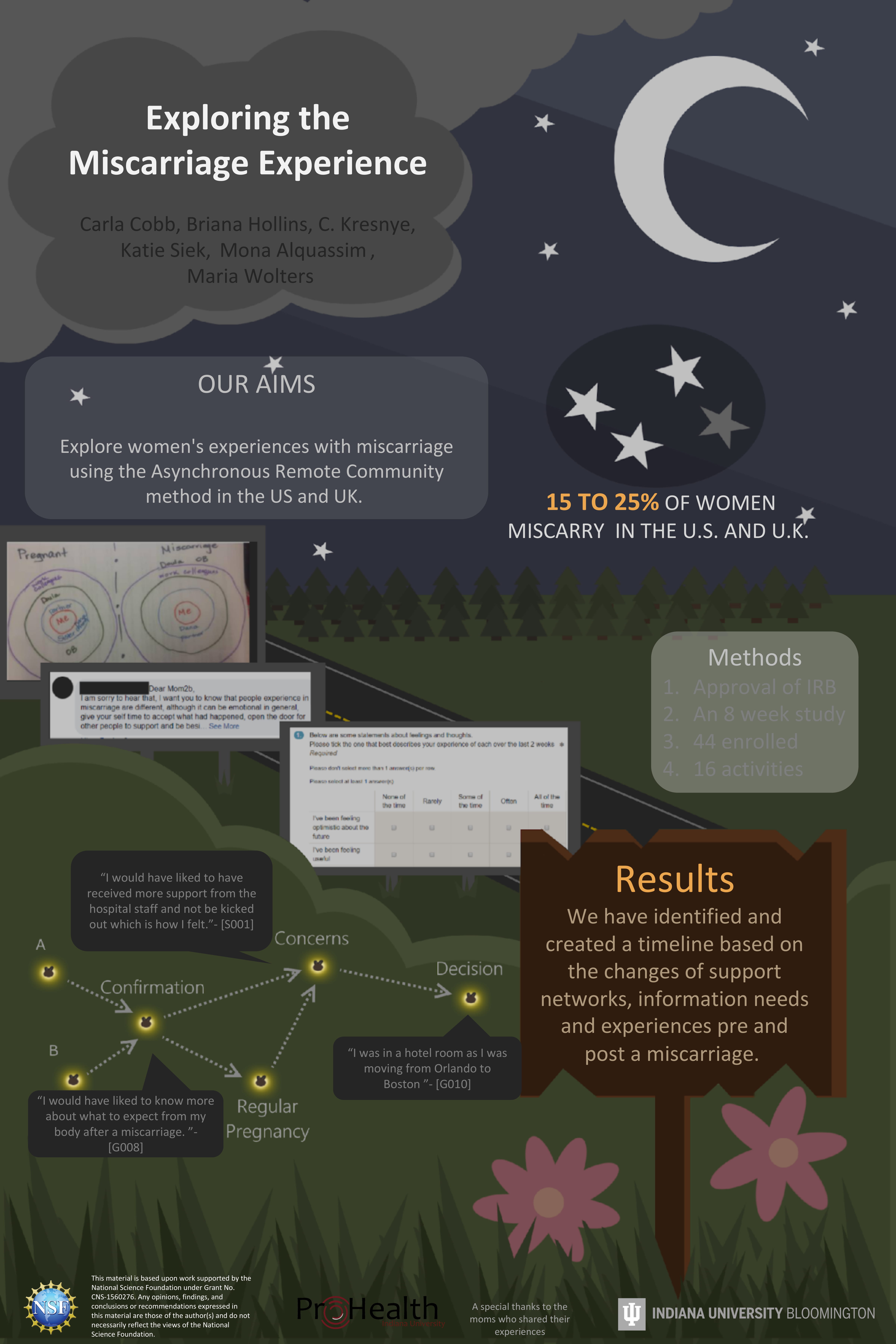
Exploring the Miscarriage ExperienceIn this paper, we explored the information and support needs of women in the United States and the United Kingdom who have experienced at least one pregnancy loss to better understand the overall experience on a more personal level. To collect and analyze data for our cross-cultural study, we employed the Asynchronous Remote Community (ARC)-based method that allowed us to interact with participants living in the United Kingdom and the United States via a social media space. Once we consented 44 participants, we engaged them in a total of 16 activities via two secret Facebook groups over a period of 8 weeks. One Facebook group was for women who have had a child since their last miscarriage and another was for women who have not had a child since their last miscarriage. Our researchers found that the women in our study’s miscarriage experiences are closely intertwined with their health care systems. We also saw that the mother's support network changed after their miscarriage, specifically through whom they consider close to them. Additionally, participant participation decreased by week seven but not significantly across all activity types. The amount of time it took for the participants to respond to the types of activities (free-text, survey, or media) varied significantly, accounting for the differences in time zones. The amount of information received during a potentially traumatizing, emotionally taxing, and confusing experience can have a positive influence on one’s experience. Our findings advocate for more informed and open communication between medical professionals and women experiencing miscarriages on a global scale. Additionally, it suggests that a change is needed in the way women are informed about their miscarriage in emergency room settings.
Brittany Davis
Neuroscience, Computer Science
DePauw University
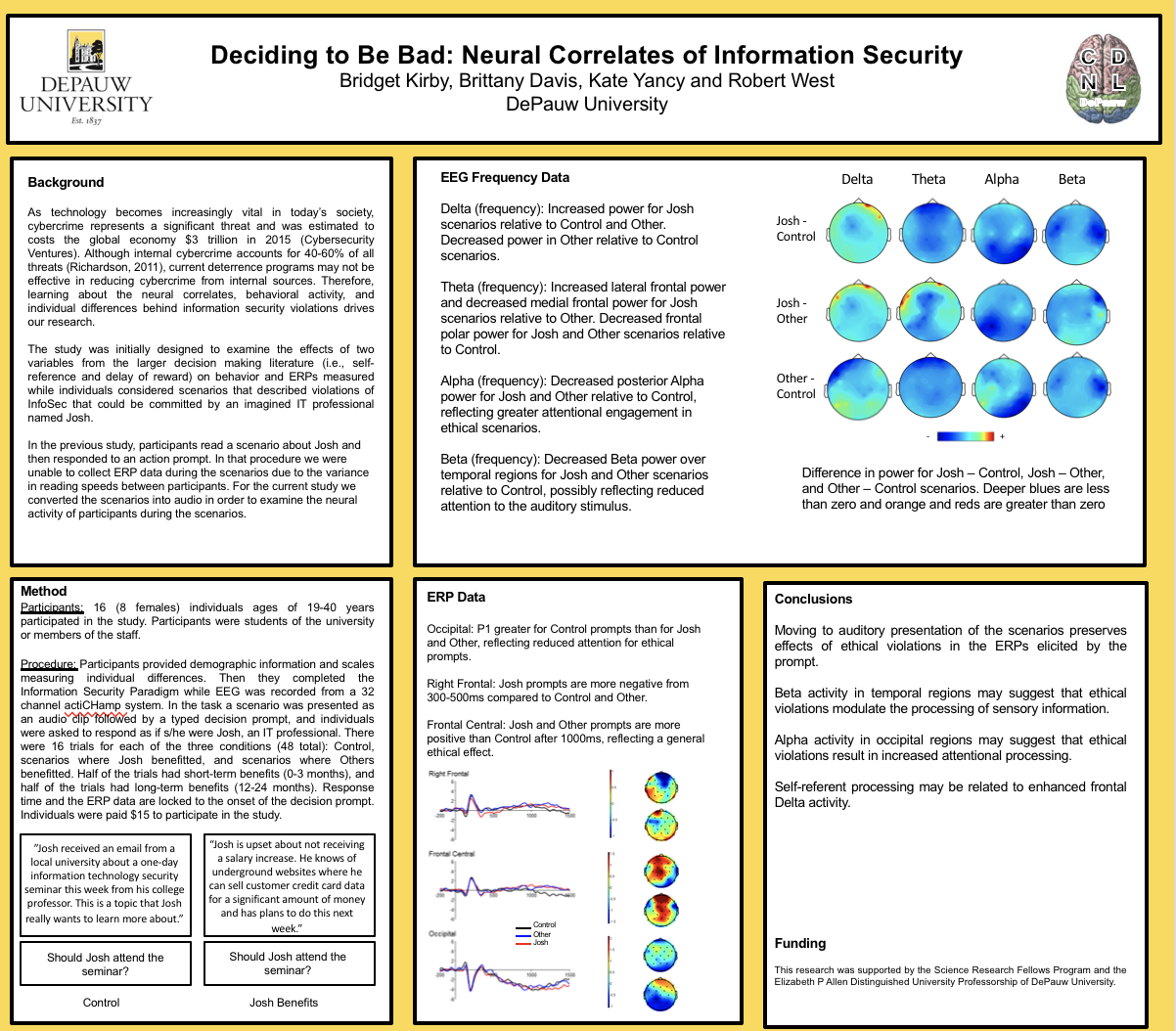
Deciding to Be Bad: Neural Correlates of Information SecurityAs technology becomes increasingly vital in today’s society, cybercrime has come to represent a significant threat to individuals, companies, and governments. Roughly 50% of violations of information security (InfoSec) result from insider threat (i.e., individuals working within the organization). Therefore, our research has sought to explore neural activity while individuals are thinking about violating InfoSec. To do this we measure brain waves (EEG) while individuals perform the information security paradigm (ISP). In this task individuals read scenarios that described violations of InfoSec that could be committed by an imagined IT professional named Josh, and are asked to decide whether or not Josh should violate InfoSec in order to receive some benefit. A limitation of our previous research represents an inability to examine neural activity while individuals read the scenarios given marked individual differences in reading speed. For the current study we presented scenarios auditorily in order to control presentation duration across individuals, and used EEG frequency based analysis to explore neural activity while individuals listened to the scenarios. The frequency data revealed effects of considering ethical violations relative to control scenarios across the Delta, Theta, Alpha, and Beta EEG frequency bands. These effects may reflect greater arousal or alertness, and a stronger focus on internal information processing than perceptual processing, when listening to scenarios that involved an ethical consideration.
Amara Edwards
Computer Science
Dillard University
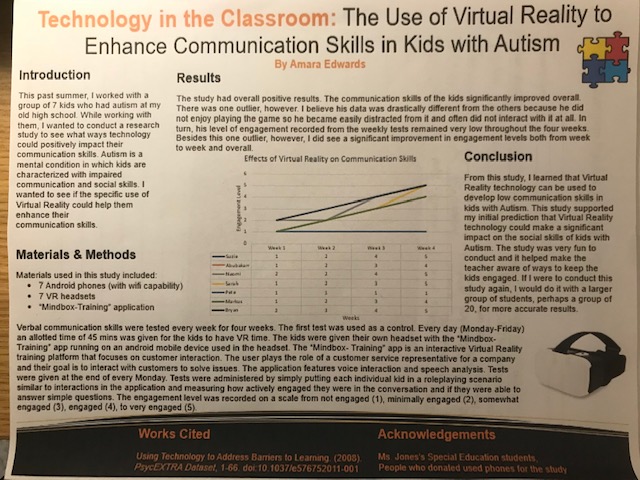
Technology in the Classroom: The Use of Virtual Reality to Enhance Communication Skills in Kids with AutismMy research project is about how Virtual Reality can enhance the communication skills of kids with autism. I see a need for this research because autism is a very common mental condition, and I want to find a way to use technology to improve the characteristically low communication skills of autistic kids. My hypothesis is that the use of Virtual Reality can significantly improve the communication skills of kids with autism over time. I believe that the potential impact of this research will be that autistic kids with initially low communication skills will start to have very high communication skills.
Anna Hawkins
Computer Science, Mathematical Sciences
Ball State University
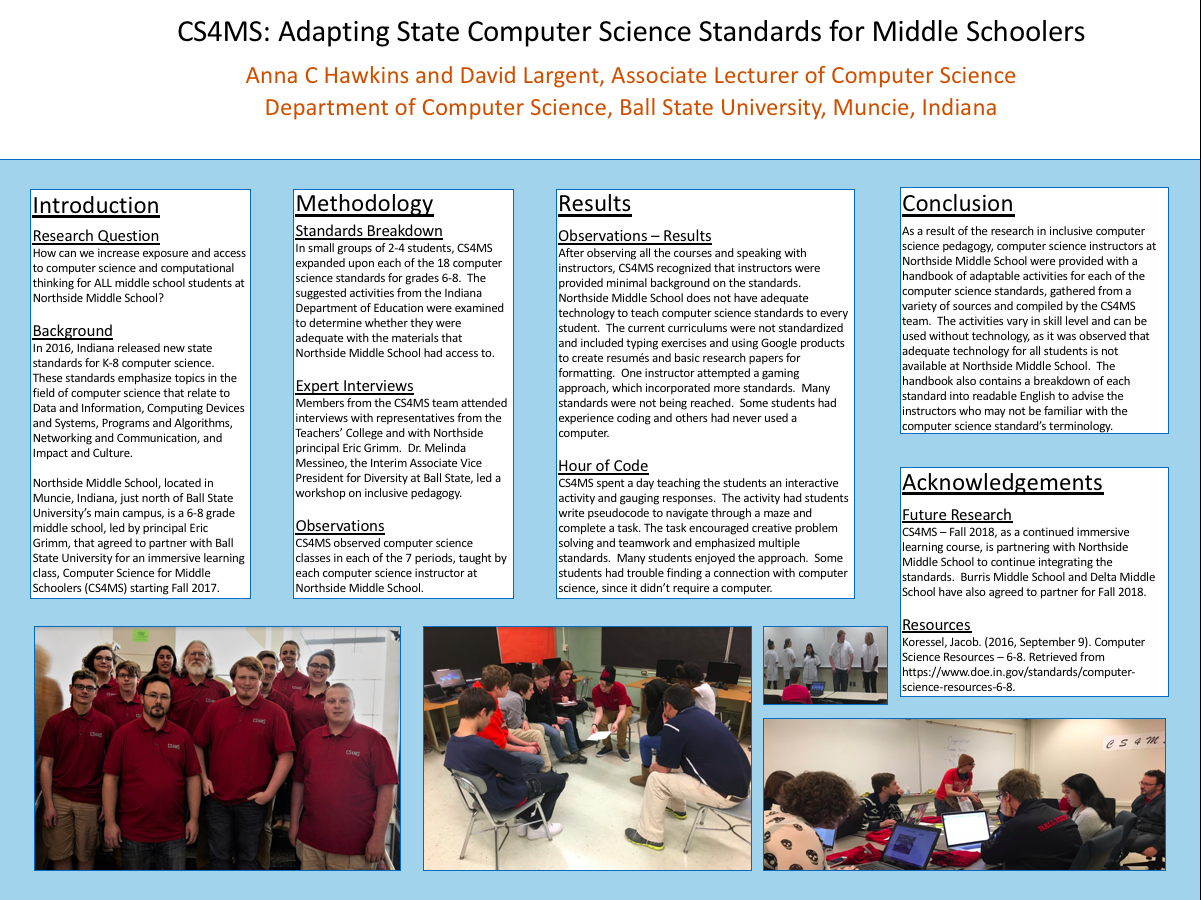
CS4MS: Adapting State Computer Science Standards for Middle SchoolersIn 2016, Indiana released new state standards for K-8 computer science. Northside Middle School, located in Muncie, Indiana, agreed to partner with Ball State University for an immersive learning class, Computer Science for Middle Schoolers (CS4MS) starting Fall 2017. CS4MS sought to answer the essential question: How can we increase exposure and access to computer science and computational thinking for ALL middle school students at Northside Middle School? CS4MS designed a handbook breaking down the standards for instructors and recommending activities that are adaptable at all levels of computer science without requiring extensive technology or materials.
Paulette Koronkevich
Computer Science
Indiana University Bloomington
Obsidian in the Rough: A Case Study Evaluation of a New Blockchain Programming LanguageBlockchains are one solution for secure distributed interaction, but security vulnerabilities have already been exposed in existing programs. Obsidian, a new blockchain programming language, seeks to prevent some of these vulnerabilities using typestate and linearity. We evaluate the current design of Obsidian by implementing a blockchain application for parametric insurance as a case study. We compare this implementation to one written in Solidity, and find that Obsidian can provide stronger safety guarantees.
Halima Monds
Computer Science
Spelman College
The Science of Happiness: Do GüdHappiness is both a psychological study, but also a practice. Millennials believe that the latest iPhone or gadget will bring them an abundance of happiness. Research on happiness renders a different finding. Psychologist Dr. Laurie Santos, a professor at Yale University, has made history with her long-standing course on “The Science of Well-Being”. This course explores the research behind happiness, but also provides habits that people can form in order to be happier. In fact this “is the most popular class in the university's 316-year history” (Bruk, 2018). Course findings reveal that experiences, not things, actually make people happier. Such findings support the development of the Do Güd app to be used to engage end-users in random acts of kindness — bringing both the recipient and doer closer to happiness.
Susan Monsey
Computer Science
Indiana University Bloomington

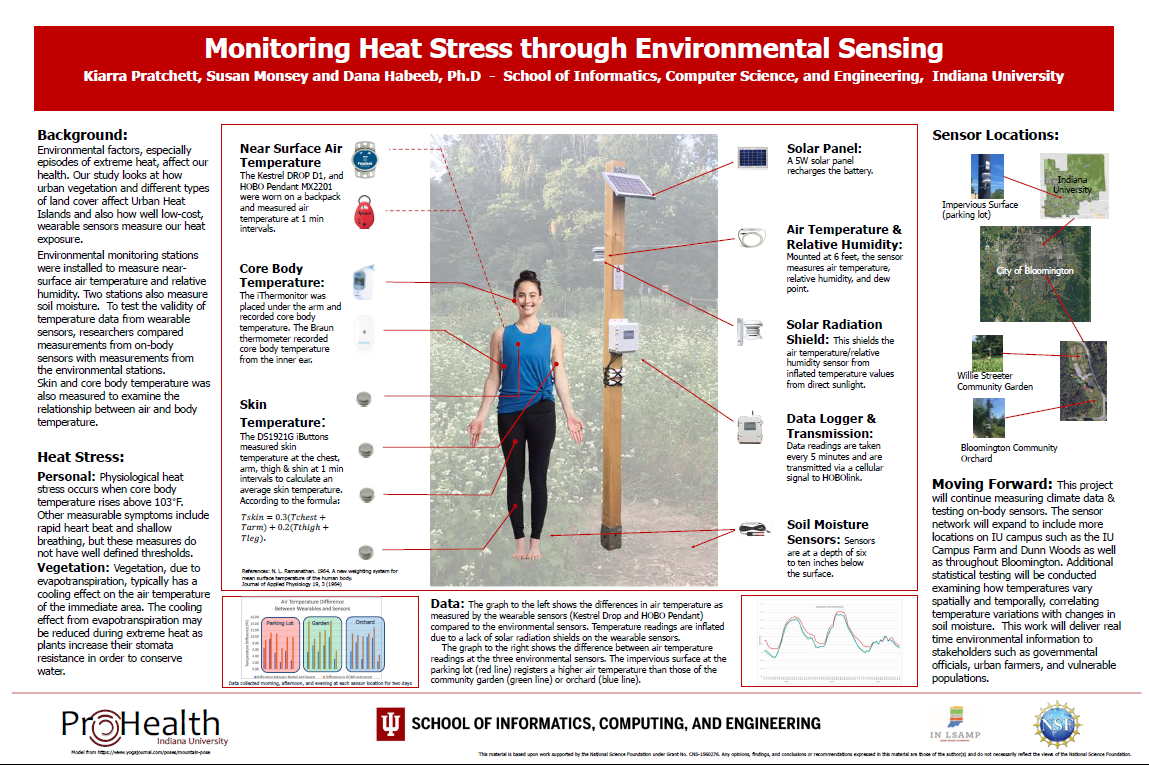
Monitoring Heat Stress through Environmental SensingEnvironmental factors, especially episodes of extreme heat, affect our health. Our study looks at how urban vegetation and different types of land cover affect Urban Heat Islands and also how well low-cost, wearable sensors measure our heat exposure. Environmental monitoring stations were installed to measure near-surface air temperature, relative humidity and soil moisture. To test the validity of temperature data from wearable sensors, researchers compared measurements from on-body sensors with measurements from the environmental stations. Skin and core body temperature was also measured to examine the relationship between air and body temperature.
Regina Rex
Computer Science
University of Wisconsin — Superior
Metrics for Efficient Environment Exploration in Robot Motion PlanningMotion planning algorithms find safe paths for robots. It has a broad range of applications from Computational Biology to Computer Graphics. State of the art sampling-based planning methods have difficulty in narrow regions. This poster presents a method for biasing environment exploration based on the size of free space between obstacles in the environment. In particular, this method is applied to Dynamic Region-biased Rapidly-exploring Random Trees (DR-RRT), a sampling-based planner that encodes the environment topology to guide exploration.
Stephanie Schoch
Computer Science, Psychology
St. Mary's College of Maryland
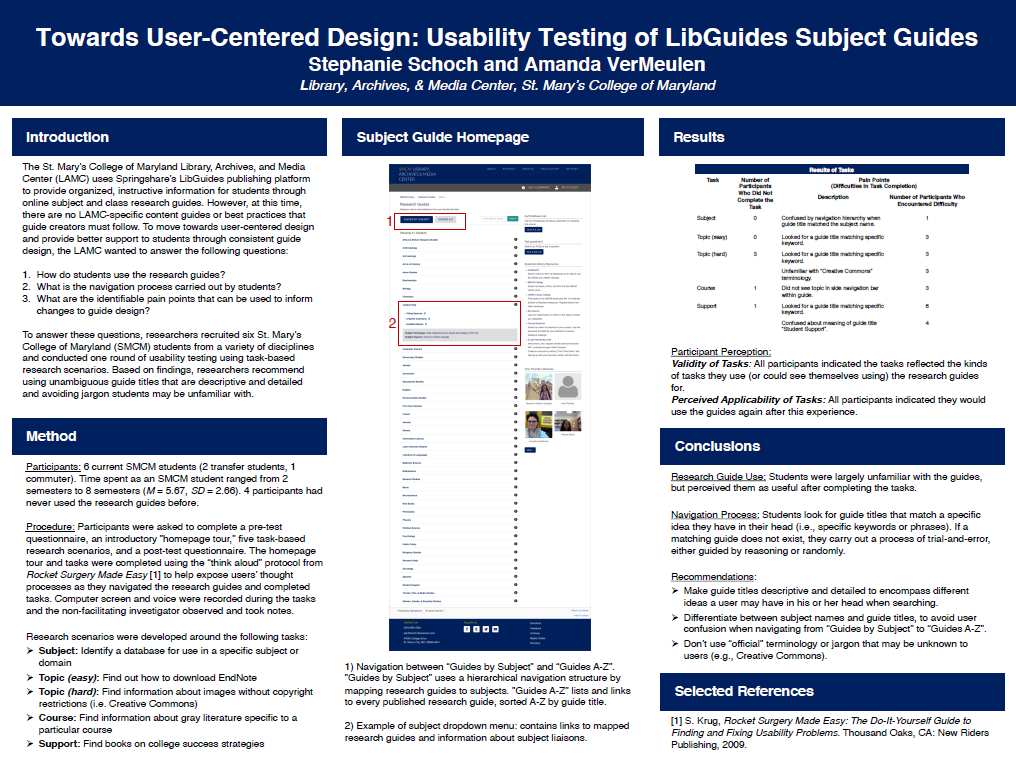
Towards User-Centered Design: Usability Testing of LibGuides Subject GuidesThe St. Mary’s College of Maryland Library, Archives, and Media Center (LAMC) uses Springshare’s LibGuides publishing platform to provide organized, instructive information for students through online subject and class research guides. However, at this time, there are no LAMC-specific content guides or best practices that guide creators must follow. To move towards user-centered design and provide better support to students through consistent guide design, the LAMC wanted to answer the following questions: how do students use the research guides, what is the navigation process carried out by students, and what are the identifiable pain points that can be used to inform changes to guide design? To answer these questions, researchers recruited six St. Mary’s College of Maryland (SMCM) students from a variety of disciplines and conducted one round of usability testing using task-based research scenarios. Based on findings, researchers recommend using unambiguous guide titles that are descriptive and detailed and avoiding “official” terminology or jargon students may be unfamiliar with.
Pi Songkuntham
Computer Science
Wesleyan University
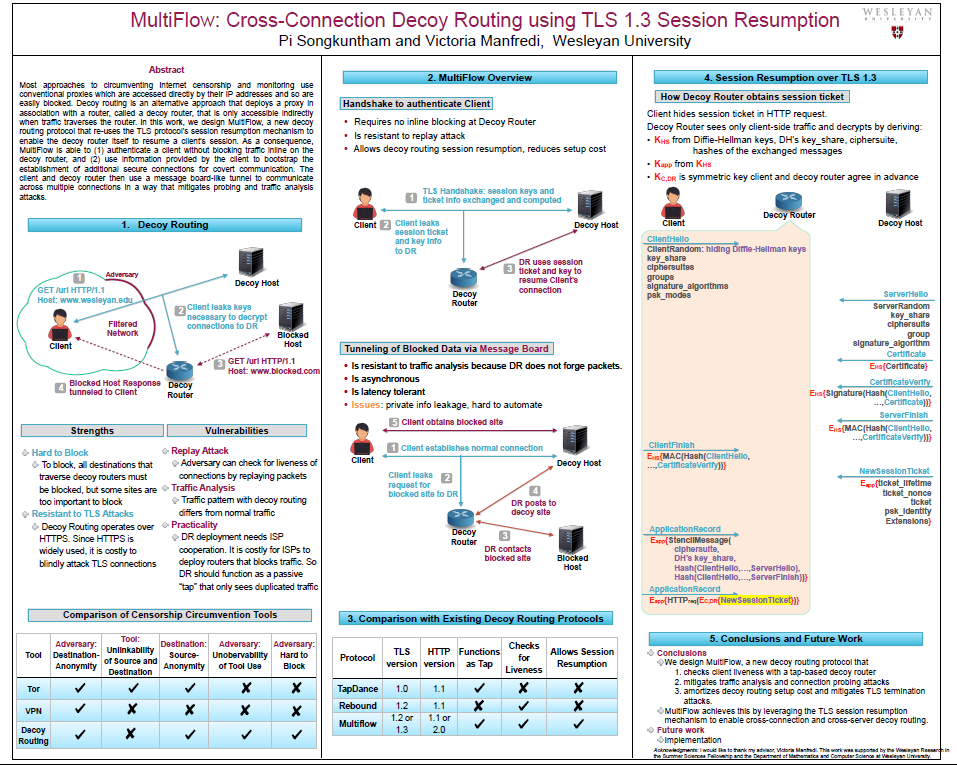
MultiFlow: Cross-Connection Decoy Routing using TLS 1.3 Session ResumptionMost approaches to circumventing Internet censorship and monitoring use conventional proxies which are accessed directly by their IP addresses and so are easily blocked. Decoy routing is an alternative approach that deploys a proxy in association with a router, called a decoy router, that is only accessible indirectly when traffic traverses the router. In this work, we design MultiFlow, a new decoy routing protocol that re-uses the TLS protocol’s session resumption mechanism to enable the decoy router itself to resume a client’s session. As a consequence, MultiFlow is able to (1) authenticate a client without blocking traffic inline on the decoy router, and (2) use information provided by the client to bootstrap the establishment of additional secure connections for covert communication. The client and decoy router then use a message board-like tunnel to communicate across multiple connections in a way that mitigates probing and traffic analysis attacks.
Katherine Spoon
Computer Science
Indiana University Bloomington
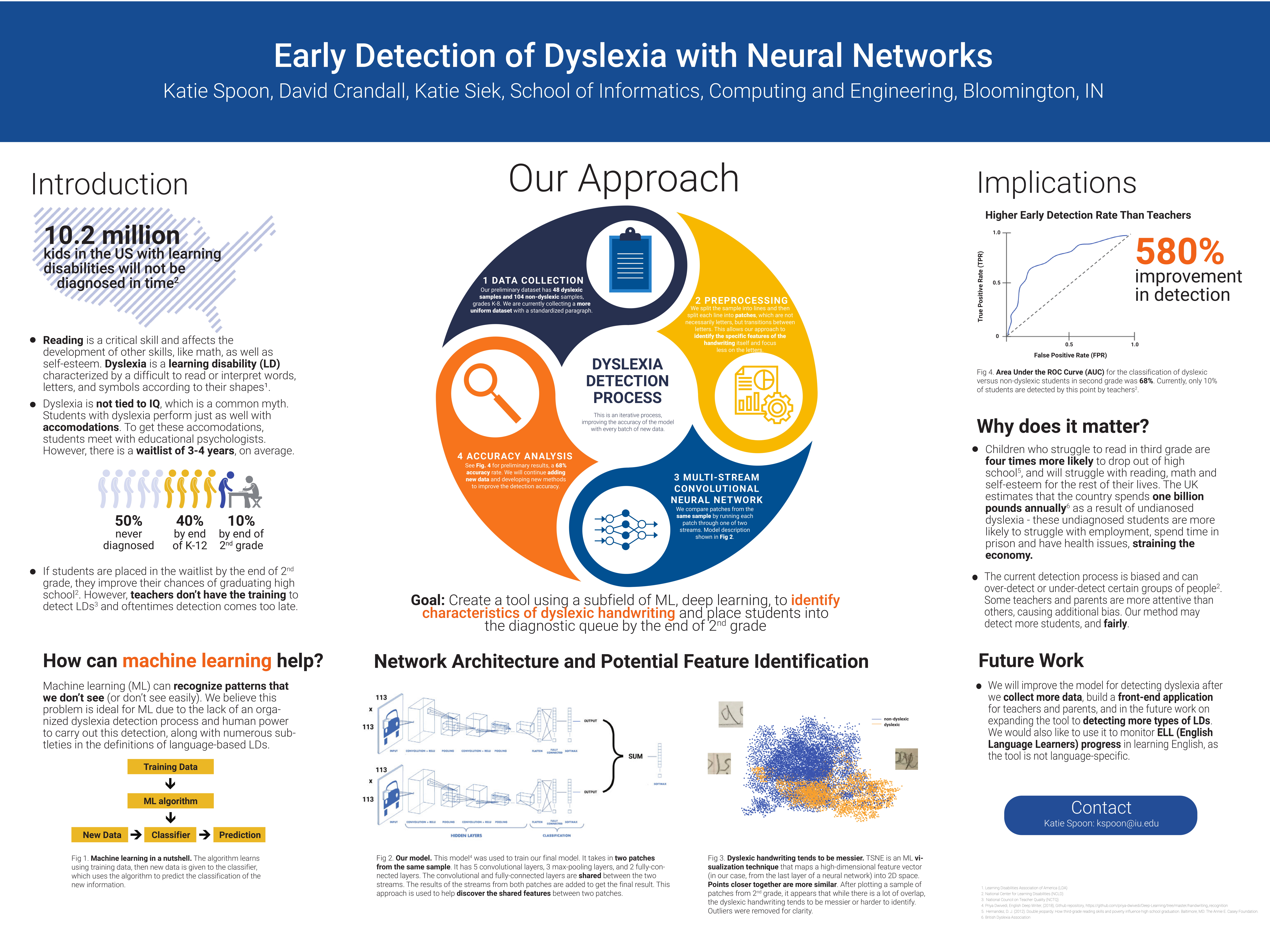
Automated Detection of Dyslexia using Neural NetworksDyslexia is a learning disability characterized by a difficulty in learning to read or interpret words, letters and symbols due to their shapes. Reading is a critical skill for all children and affects the development of most other skills (including math), as well as self-esteem. Because of this, early detection of dyslexia is essential. With the proper accommodations dyslexic students perform well, but in order to get those accommodations they need to be properly diagnosed by an educational psychologist. The wait time to be diagnosed is 3-4 years. We propose a tool that uses a multi-stream deep convolutional neural network to classify children’s handwriting as either possibly dyslexic or not, so that in the years spent waiting to be diagnosed, the child’s family and teachers are aware that the child may have dyslexia. The results show this could be a useful addition to the classroom; our baseline model performs with an accuracy of 68% in second and third grade handwriting. By adding a simple front-end we could make the early detection of dyslexia accessible to teachers and parents. With one photo of a child’s handwriting, they could receive a rough estimate of that child’s risk of dyslexia.
Mercedes Williams
Computer Science
Coppin State University
Keep CleanUsing technology (mobile app), our project enables local residents and pedestrians to help keep Baltimore County clean. The mobile app will allow users to log in to their accounts, view data, and take pictures of PLRs which will be geo-tagged, analyzed, and displayed on a map within the app according to its latitude and longitude coordinates. The web app will allow users to view additional information about the project, manage their accounts, and view and download statistical data. Keep Clean received a grant from the Abell Foundation to continue our research and move forward with Keep Clean.